A new wave of AI-powered malware is infiltrating organizations worldwide, disguised as legitimate software and carrying the potential for widespread disruption.
Cybersecurity researchers at Trend Micro warn that the trojan, tracked as EvilAI, poses as productivity or AI-enhanced utilities with professional interfaces and valid digital signatures.
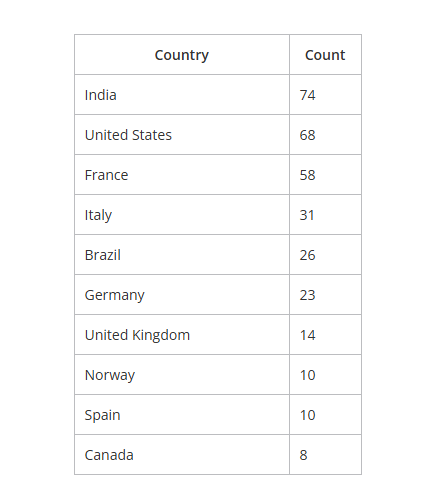
The deception has enabled the malware to penetrate both corporate and personal systems across multiple continents. First detected in late August, EvilAI infections have already appeared in Europe, the Americas, and the AMEA region, with early telemetry showing more than 100 confirmed cases. India has reported 74 incidents, followed by the United States with 68 and France with 58.
The malware’s mechanics are rooted in mimicry. Malicious apps such as Recipe Lister and PDF Editor deliver functional features to gain trust, while simultaneously launching hidden JavaScript payloads via Node.js. Attackers further enhance credibility with stolen or newly registered code-signing certificates, making the software appear “verified” to end users.
The scale is broad and indiscriminate, with industry telemetry showing manufacturing with 58 incidents, government services with 51, and healthcare with 48. Technology and retail sectors have also been hit, underscoring the malware’s reach.
Trend Micro says the malware uses AES-encrypted channels to maintain real-time communication with C2 servers. Attackers can exfiltrate browser data, enumerate security tools via registry queries, and deploy additional payloads through persistent scheduled tasks that blend in with legitimate Windows processes.
“Based on telemetry, the attacker created copies of both the ‘Web Data’ and ‘Preferences’ files from Microsoft Edge and Google Chrome browser profiles.”
The campaign remains active and appears to be operating as a stager, establishing access for secondary infostealers that remain unidentified. Cybersecurity researchers caution that the sophistication and speed of EvilAI’s spread reflect the increasing weaponization of artificial intelligence by threat actors.
“This lack of clarity poses a significant risk. Without knowing what’s being delivered post-infection, organizations cannot fully assess the damage or implement effective containment. It also suggests the campaign is still active and evolving, with attackers possibly testing or rotating payloads in real time.
The rise of AI-powered malware like EvilAI underscores a broader shift in the threat landscape. AI is no longer just a tool for defenders – it’s now being weaponized by threat actors to produce malware that is smarter, stealthier, and more scalable than ever before. In this environment, familiar software, signed certificates, and polished interfaces can no longer be taken at face value.”
Disclaimer: Opinions expressed at CapitalAI Daily are not investment advice. Investors should do their own due diligence before making any decisions involving securities, cryptocurrencies, or digital assets. Your transfers and trades are at your own risk, and any losses you may incur are your responsibility. CapitalAI Daily does not recommend the buying or selling of any assets, nor is CapitalAI Daily an investment advisor. See our Editorial Standards and Terms of Use.


